AccessIT Group’s vCISO Services provide the expertise of a Certified Chief Information Security Officer (C|CISO), backed up by a team of seasoned security professionals with specialist skills.
We help organizations of all sizes regain control and assist in the development of an industry leading cybersecurity program developed from the top down.

Reasons to Hire a vCISO from AccessIT Group
Full-time CISOs are Hard to Find
Our vCISO services provide the missing link to today’s cybersecurity uncertainties that are placed on organizations who struggle to afford or identify qualified experts.
Regulatory Requirements are Difficult to Interpret
We provide expert help to sort out increasingly complex regulatory and statutory requirements, leaving executives time to focus on critical business decisions.
Technology is Often Misaligned
Working with AccessIT Group gives you the benefit of direct access to long-standing, deep partnerships with leading technology vendors that will help you prioritize and complete your tech stack.
Out-of-date Governance Policies
Our cybersecurity professionals are experienced in writing policies and standards that help define and enforce governance initiatives, applying a top-down approach.
Too Many Frameworks to Choose From
Receive guidance from industry experts on choosing and implementing a framework that fits your organization’s current and future goals and objectives.
Determining Cyber Risk is Daunting
We assist organizations to identify, classify and quantify critical assets and data, determining risk posture and allowing for the effective justification and prioritization of security controls.
We deliver the skills and expertise you need to help identify, prioritize, and mitigate cybersecurity risk.
Our vCISO experts are industry certified professionals with decades of experience. Not only can we provide the services of our highly qualified and certified vCISOs, but also expertise across the entire cybersecurity ecosystem with qualified product and solution professionals at the ready to support your organization’s cyber hygiene and risk mitigation objectives.




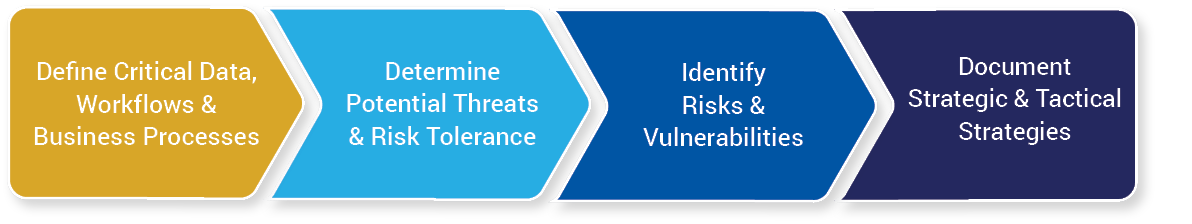
Our Methodology
As a strategic partner, AccessIT Group takes the time to understand your organization’s mission, goals, and objectives to better map a cohesive alignment between the business and the critical people, processes, and technologies it depends on. We dig into your cybersecurity governance processes, technical controls, and countermeasures and help map strategic and tactical cybersecurity plans to ensure they enable overall organizational success.
Request a Quote
To request a proposal or quote for our Virtual CISO Services, please use the form below.