Beyond IT: The Importance of Non-Technical Staff in Incident Response

Why Non-Technical Staff Need to Play a Role in Incident Response Exercises In today’s digital landscape, cybersecurity threats are a major concern for organizations of all sizes. While IT and Security departments are on the front lines defending against these threats, the responsibility of maintaining a secure environment extends beyond the technical team. Non-technical employees play a critical role in maintaining organizational security and must be prepared to respond to incidents. Incident response tabletop exercises serve as one of the most effective ways for preparing all staff members, regardless of their technical expertise.. These exercises simulate real-world scenarios, allowing non-technical personnel to understand their roles, improve their response strategies, and enhance their overall awareness. Here’s why involving non-technical participants in these exercises is not just beneficial, but essential for comprehensive organizational security. Broadening Awareness (Understanding the Impact of Cyberthreats) Non-technical staff often do not realize the potential impact of cyberthreats on their daily work and the rest of the organization. Tabletop exercises help to make it clear just how organizational risk affects everyone. Visualizing Scenarios Through simulated cyberincidents, non-technical employees can see firsthand how a breach can unfold and disrupt various aspects of the business—from finance and human resources to marketing and customer service. Culture of Security The term “culture of security” gets used a lot. Awareness Training, Phishing Simulates and many other things play a part for sure. Having your stakeholders and decision makers participate in tabletop exercises instills a sense of responsibility. It emphasizes that security is everyone’s responsibility company wide. Everyone plays a role in protecting company data, finances, fellow employees, and customers. Proactive, Early Response Tabletop exercises can teach non-technical staff to recognize early signs of potential security incidents. This awareness leads to faster reporting to IT teams, potentially averting a crisis if someone notices something like unusual system behavior. Improve Communication Across Departments During a real incident, communication across departments is vitally important. Tabletop exercises provide a practice arena for this communication between different teams. During an actual incident, information needs to flow swiftly and accurately so that people know what to do based on their role in the company. Improving Incident Response Plans Chances are most employees have never looked at the Incident Response Plan, and it wouldn’t mean much to them if they did. When non-technical staff participate in tabletop exercises, they often provide their own perspectives on how responses might play out. This information can be written into the plan to make it more complete and meaningful. Meeting Compliance Requirements Understanding Legal and Regulatory Obligations: Many industries are subject to regulations that require a proactive approach to cybersecurity. Sometimes there are complex decisions to be made regarding incident and breach notifications. Knowing in advance who has that information, and how they are to make decisions. What if all the compliance documentation is saved in a file folder that no one can get to? Conclusion Someday, we may be able to declare our independence from cybersecurity threats, but until then, we encourage you to practice your organizations communication, collaboration and decision making to stay prepared. The AccessIT Group Approach We develop scenarios that are topical, using recent real-world events that could happen to your company. Our goal is to facilitate and exercise that encourages collaboration and creativity among the participants. We want to help every stakeholder be prepared, and confident. Contact us for more information about our Incident Preparedness Services. By: Peter Thornton – Senior Security Consultant – CISSP | HCISPP | ISSMP | PMP | CISA | QSA
Preparing for Your First PCI DSS 4.0 Assessment

Super Easy, Barely an Inconvenience: Preparing for your first PCI DSS 4.0 Assessment Diving headfirst into any major project without some preparation is not for the faint of heart, and your first PCI DSS 4.0 Report on Compliance will be a major project. The result of not planning can turn into a mad dash to patch systems, gather evidence, and contact the right people. Schedules fall behind and costs get out of control. Let me help you avoid some of that trouble by offering some tips to help prepare for a less troublesome PCI experience. Here are 10 steps you can take now to help prepare for your PCI DSS 4.0 assessment: 1. Get your team together Your company’s first PCI DSS 4.0 assignment is likely to be a large project involving multiple departments. Make sure you communicate the importance of the assessment effort and have people available to participate in interviews, gather evidence, and remediate any gaps found along the way. 2. Roles and responsibilities Along with getting your team ready, roles and responsibilities must be identified for all of the PCI DSS requirements. Depending on the size of your organization, this may be a big task. 3. Scope the environment Determining the scope of your PCI DSS assessment early is critical for a good start. All systems and processes that store, process, or transmit cardholder data are evaluated for compliance. To accurately define your scope, start by identifying the flow of cardholder data within your organization. Map out every point where cardholder data enters your environment, how it moves through and is processed within your systems, and where it exits or is stored. Include any systems that connect to your cardholder data environment or can impact your cardholder data environment. The scoping exercise is a requirement that your company will need to perform at least yearly from now on. 4. Vendor Roundup Your company may be using Third Party Service Providers (TPSP) to manage some or all of the payment, or IT functions. The TPSPs to focus on here are not only those that have access to the cardholder data environment but also those that manage in-scope systems or could impact security. This could include your MSP, Web Hosting Provider, Cloud Provider, and many others. Make a list of your TPSPs, and gather all of their PCI compliance documentation such as AOCs, Responsibility Matrix, and any other documentation that states how the TPSP is managing security and compliance on your behalf. 5. Inventory An accurate and thorough inventory of your systems should include details about the function and use. The inventory may include things you might not think of: • Trusted Keys and Certificates • Cryptographic Cypher Suites and Protocols • Software, including custom, bespoke, and third-party applications. • Media with cardholder data. • All hardware including Workstations, Wireless Access Points, HSMs, and both physical and virtual components. 6. Watch out for End of Life Any hardware or software that is out of date and can’t receive security updates or patches will be a problem. Suppose your company has a legacy system that can’t be updated because of some business constraint, a compensating control may be needed. Compensating controls need to be implemented and tested before the assessment begins. Discovering an out-of-date system during the assessment may cause a significant delay in the project and possibly non-compliance. If you plan to use a compensating control for a legacy system, check with your QSA company before the assessment begins for more guidance. 7. Penetration Tests Internal and external penetration tests should be started early, preferably before the assessment begins. If the penetration tests are started late, and remediation is required, then the assessment may be delayed. 8. ASV Scans Before PCI DSS 4.0, not all E-Commerce assessments required ASV scans, but now they do. SAQ A and SAQ A-EP will require ASV scans. The ASV scan must be a PASSING scan from an ASV company, so get started early to allow time for remediation of gaps that are found. 9. Policies and Procedures Gather up your company’s relevant policies and procedures. Policies must be reviewed and updated annually, so make sure they are current. There needs to be a policy for every applicable PCI requirement. If your policies need work, reach out to your QSA company for help. 10. Look to the Future Some new requirements in PCI DSS 4.0 are future-dated, taking effect in March of 2025. Don’t wait to start on these new requirements! Some of them will take a great deal of time to implement. AccessIT Group can help prepare for the new requirements by providing a PCI DSS 4.0 workshop for your company. Planning for your 2024 and 2025 PCI assessments will save a lot of time. By: Peter Thornton – Senior Security Consultant – CISSP | HCISPP | ISSMP | PMP | CISA | QSA
Securing Payments: The Strategic Advantage of Outsourcing for PCI DSS Compliance and Mitigating Third-Party Cybersecurity Risks

Cybersecurity is not only a team sport—it’s a multi-team sport. The complexity of cybersecurity as well as resource constraints make it nearly impossible to do business without help from third-parties. Utilizing third-party service providers for PCI DSS compliance offers several significant benefits, such as scope reduction. By outsourcing certain functions involving the handling, processing, or storage of cardholder data to PCI DSS compliant third parties, merchants can effectively reduce the complexity and extent of their own PCI DSS compliance requirements. Scope reduction is advantageous as it narrows down the merchant’s environment that needs to be secured and assessed, decreasing the burden of security audits and lowering costs. Specialized third-party providers often have well-established security infrastructures and expertise in data protection, which can improve your overall security posture. Outsourcing may allow merchants to focus more resources on core business activities, with less time and money spent on payment security. It is very important to remember that while third-party service providers can reduce the scope, merchants retain ultimate responsibility for ensuring that their providers are compliant and that the cardholder data is protected throughout the entire transaction process. Failing to properly manage third-party service providers poses significant cybersecurity risks for any organization. Third-party service providers often have access to or manage sensitive data, systems, or infrastructure. If these service providers are not adequately vetted and monitored for compliance with cybersecurity standards, such as the PCI DSS), HIPAA, and others. A breach in a third-party service provider’s system can have serious repercussions for a merchant under the PCI DSS framework. As merchants often rely on third-party service providers for processing, storing, or transmitting cardholder data, a compromise in the provider’s security can directly threaten the confidentiality and integrity of sensitive payment information. Such a breach not only exposes the merchant to potential data theft and financial fraud but also to significant compliance risks. Under PCI DSS, merchants are responsible for ensuring that all entities handling their cardholder data maintain compliance. A breach of a third-party service provider that compromises your data could lead to fines, increased scrutiny in future audits, and reputation damage. If a service provider is breached due to non-compliance or lax security measures, the merchant can be held accountable for the resulting data loss. According to its annual study of third-party risk, The Ponemon Institute—a research center dedicated to privacy, data protection, and information security policy—says that most organizations consider themselves at risk for security breaches caused by third parties, and that risk is increasing. The findings of the study are interesting to read and can be found here: The 2022 Data Risk in the Third-Party Ecosystem Study For PCI DSS compliance, and to ensure the security of your data, review the Attestation of Compliance and the Responsibility Matrix for your third-party service providers at least annually. By carefully examining these documents, merchants can ensure that their third-party service providers are adhering to necessary security standards, thereby safeguarding their customers’ payment card information and maintaining the integrity of their business and your data. Remember, ultimately, your company may be held responsible for any data breaches, the third-party service providers are handling YOUR data. For starters, keep a list of your third-party service providers. The list should at least include, the provider contact information (for incident response), a description of the services provided, and which security requirements they are responsible for, plus compliance dates. Once you get the Attestations of Compliance from your service providers, do not just file it and move on. Here are some suggestions for reviewing the AOCs. • Look for a description of the services provided. This document should explain what the service provider does to meet your company’s PCI DSS requirements. • Confirm Service Provider Details: If the AOC is from a service provider, make sure it’s a service provider AOC and not a merchant AOC. If the TPSP fills out an SAQ, it must be SAQ-D. • Check Service Coverage: The document should list the specific services covered under the PCI DSS assessment. The services you subscribe to from the provider must be stated. • Review Assessment Dates: PCI DSS compliance is an ongoing process, not a one-time event. The AOC should have recent dates indicating that the assessment is up-to-date. • Assessor Credentials: The AOC must be completed by a qualified assessor. This could be a Qualified Security Assessor (QSA) or an approved Internal Security Assessor (ISA). • Examine PCI DSS Requirements Compliance: Each requirement of the PCI DSS should be addressed in the AOC, with a clear indication of whether it is ‘in place” or “not applicable”. Any requirements listed as not applicable should have a specific reason and that reason should be consistent with the services they are providing to your company. • Signature and Attestation: The document should be duly signed and dated by the service provider and the assessor, attesting to the accuracy of the information. The signature from the service provider should be a person who has the authority and accountability to sign such as CISO, CFO, or Director of Security. Ideally, TPSPs will also provide a Responsibility Matrix. This document spells out in detail what requirements they are responsible for, what you are responsible for, and which are shared. • Clarify Responsibilities: The matrix should detail which party is responsible for each aspect of the PCI DSS requirements. This clarity is essential to ensure there are no gaps in compliance. • Alignment with AOC: Cross-reference the responsibilities in the matrix with the AOC so the information is consistent. • Comprehensiveness: The matrix should cover all PCI DSS requirements. This includes aspects such as data encryption, access controls, and network security. If any requirements are not applicable, again, there should be a valid reason, and it should be consistent with the service your company is paying for. In conclusion, the real reason to keep up to date with TPSP documentation is not just to make sure they are compliant, but to understand how the service they provide to
Security and Privacy: Stick to the Script

The payment page of one well-known e-commerce site recently visited by the author contained 16 third-party scripts, including some from companies that are well-known for siphoning personal information. There are security and privacy reasons to provide stronger safeguards from scripts that can be compromised by threat actors to steal payment information. Effectively managing and overseeing the scripts that operate on websites, particularly those that gather personal data, is crucial. Data protection regulations like the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA) have significant implications for the monitoring and governance of webpage scripts. A proactive approach may be a legal obligation as well as maintaining user trust. Focusing on payment pages, the Payment Card Industry Data Security Standard (PCI DSS) is continuing to improve security, working along with partners and payment brands to keep up with new payment technology and emerging threats. This post will delve into two specific updates within PCI DSS v4.0: requirements 6.4.3 and 11.6.1. These are future dated requirements which will be considered Best Practice until March 2025 and mandatory thereafter. Requirement 6.4.3: Minimizing Attack Surface on Payment Pages Overview: This requirement focuses on ensuring that the Payment Page remains secure, particularly concerning the JavaScript components that are present. Key Components: Managing JavaScript: Every piece of JavaScript present on the Payment Page needs to be closely monitored and managed. Any third-party scripts should be examined for security vulnerabilities. Regular Audits: Periodic audits of the Payment Page should be conducted to identify and restrict any questionable scripts. Benefits: By focusing on the proper management of JavaScript on the Payment Page, this requirement aims to reduce potential entry points for malicious actors. This way, the security of credit card data remains uncompromised. 2. Requirement 11.6.1: Detecting Tampering on Payment Pages Overview: Requirement 11.6.1 ensures that any unauthorized changes or tampering to the Payment Page are quickly detected, and relevant stakeholders are promptly alerted. Key Components: Continuous Monitoring: Implement mechanisms to continuously monitor the Payment Page for any unauthorized changes. Alert Mechanisms: In the event of any suspicious or unauthorized changes, the system should automatically generate and send alerts to the security team. Audit Logs: Maintain detailed logs of all changes made to the Payment Page. This ensures an auditable trail and helps in tracing any unauthorized access or changes. Benefits: By proactively monitoring and alerting on changes to the Payment Page, organizations can quickly detect and respond to potential security breaches, ensuring the trustworthiness of their payment systems and the safety of customer data. Conclusion PCI DSS v4.0, through requirements like 6.4.3 and 11.6.1, stresses the importance of proactive and reactive measures in safeguarding cardholder data. The emphasis on both reducing vulnerabilities on the Payment Page and actively detecting unauthorized changes is a testament to the comprehensive approach that this standard advocates. It’s crucial for organizations to fully grasp and implement these requirements, not just for compliance but to build a culture of cybersecurity and retain the confidence of consumers. How can your company implement these new requirements? Reach out to AccessIT Group and one of our experts will help you find the right solution. By: Peter Thornton – Senior Security Consultant – CISSP | HCISPP | ISSMP | PMP | CISA | QSA Contact us for more information about our cybersecurity solutions.
Unwrapping Social Engineering: Stay a step ahead of cybercriminals this season
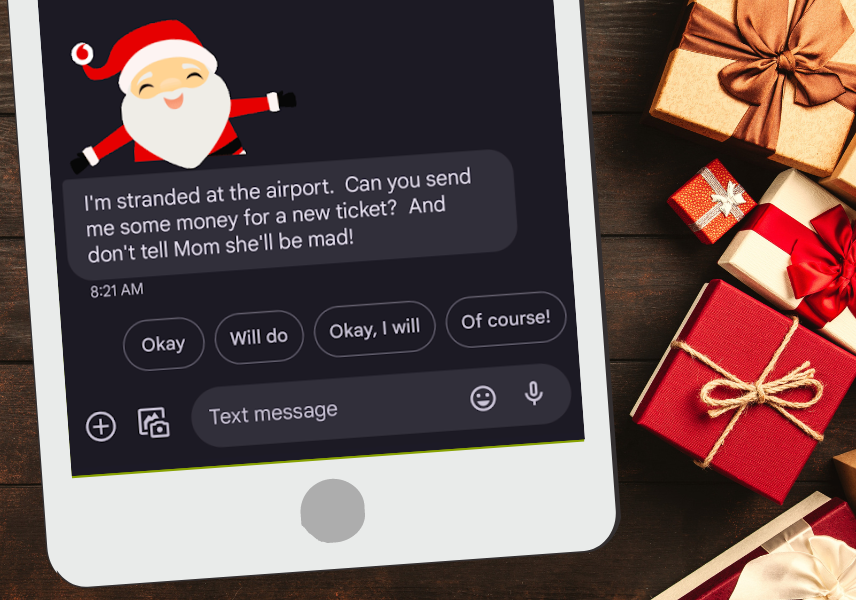
What do natural disasters and holidays have in common? That is when criminals love to scam people using social engineering tactics. Why? Because people are vulnerable at those times. We don’t know when the next natural disaster will strike, but we do know when the holidays will be upon us. The winter holiday season is a time of togetherness, festivity, anxiety, travel confusion, and stressful last-minute shopping. Those human conditions create a time when we are vulnerable to social engineering – even though we would normally be aware. Cybercriminals are ready to exploit those vulnerabilities that emerge during this time of year. Social engineering, a manipulative technique that preys on human psychology, becomes particularly common and effective during the holidays. When emotions run high, our guard can be let down. Let’s explore how social engineering plays a role in winter holiday cybersecurity scams. Help me get home! Beware of Impersonation Scams. One of the most insidious tactics cybercriminals employ during the winter holidays is impersonating family members. Imagine getting a phone call from a supposed relative, stranded somewhere, and in need of money to get home. Scammers play on emotions, fabricating scenarios that tug at the heartstrings, such as a family member stranded in a foreign country, facing a medical emergency, or experiencing financial distress. Who wouldn’t want to help a family member in need? During the holidays, people are more likely to be emotionally vulnerable, making them susceptible to such manipulative tactics. Cybercriminals gather information from social media and other online sources to personalize their messages, making them more convincing. Be skeptical of unexpected or urgent requests from family members, especially if they ask for sensitive information or money. Always verify the person’s identity by checking in with a trusted source, like checking with the rest of the family to see if they’ve heard anything about the situation. The scammer will more than likely stress the need for secrecy like “Don’t tell mom, she’ll be really upset.” Black Flag Friday! Social Engineering in Online Sale Scams. The winter holiday season is synonymous with gift-giving, and the quest for the perfect present often leads to online shopping sprees. Cybercriminals seize this opportunity to deploy social engineering tactics through fake online sales—picture this: a hard-to-find item at a great price listed for sale on social media. During the holidays, the desire to find the best deals may override the usual cautiousness individuals exercise when shopping online. Scammers can even create fraudulent e-commerce websites that mimic the appearance of well-known retailers, complete with eye-catching banners and too-good-to-be-true discounts. These sites may even use social engineering techniques, such as fake customer reviews and countdown timers, to create a sense of urgency. Scammers have manipulated online search results so that a fake website appears above a real shopping site. Even the best of us can click on the fake listing if we aren’t extra careful. To safeguard against online sale scams, scrutinize the legitimacy of the website before making a purchase. Remember, if a deal seems too good to be true, it probably is. Stay alert, shop wisely, and protect yourself from falling victim to holiday shopping scams. Planes, Trains, and Trickery: Social Engineering and Exploiting Holiday Wanderlust. Holiday travel opens a new avenue for cybercriminals to employ social engineering tactics. Scammers may send fake travel alerts, impersonate airlines, or create fraudulent booking confirmations. With the excitement of travel plans, individuals are more likely to overlook potential red flags, making them vulnerable to falling for these scams. Before clicking on any travel-related links or providing personal information, double-check the authenticity of the communication. Verify details directly with the airline or travel agency through their official website or contact information. If you are using a short-term rental service like VRBO or Airbnb, keep the transaction on the website. Don’t accept an offer to save money by “taking the transaction offline.” A Special Offer! Social Engineering in Phishing Attacks. Phishing attacks, a prevalent form of social engineering, get a boost during winter holidays. The high volume of email ads and special offers makes it easier for criminals to sneak in their phishing messages. These messages may contain urgent requests for personal information or prompt recipients to click on malicious links. During the holidays, people are more likely to be shopping online, and looking for bargains, making them susceptible to phishing attempts. Be careful when receiving emails with special holiday offers. The phishing emails may look like just what you want, but the link it contains may lead to a malicious website. Give me that Gift Card! The Untraceable Payment. Has any legitimate business ever asked you to pay by sending the numbers from an iTunes, or Amazon gift card? Very unlikely. Scammers use this trick to take your money in a sneaky way. By asking you to send them the numbers from a gift card – even multiple gift cards, they get the value of the card and you’re left holding the bag. The scammers will build up a sense of urgency. They need that gift card number now or you’ll be in big trouble, or you’ll miss out on this great deal. Only use gift cards for their intended purpose – gifting – and never give anyone online or over-the-phone gift card numbers and PINs. AI or human? Identifying Fake Text Messages. Artificial Intelligence helps all types of social engineering become more potent by crafting very convincing and customized messages. AI can create realistic pictures and even mimic individuals. Discerning between real interaction and AI is becoming more and more difficult. Defending against AI assisted criminals requires a multi layered approach that starts with user education and collaboration with security experts. This holiday season, give the best gift of all – the gift of security awareness, so that the only surprises we get bring joy. Stay aware, inform others, and have a happy and safe holiday season! By: Peter Thornton – Senior Security Consultant – CISSP | HCISPP | ISSMP | PMP | CISA
Targeted Risk Assessments in PCI DSS 4.0: A Closer Look

The Payment Card Industry Data Security Standard (PCI DSS) has evolved over the years to provide a robust framework for securing cardholder data. With the advent of PCI DSS 4.0, the focus has shifted towards a more flexible, outcome-driven approach that prioritizes securing data rather than just complying with a checklist of requirements. A crucial component of this updated framework is targeted risk assessments. The PCI DSS has removed the requirement for an organization-wide risk assessment and replaced it with targeted risk analyses for specific controls. What Are Targeted Risk Assessments? In the context of PCI DSS 4.0, targeted risk assessments involve a systematic and detailed evaluation of potential threats and vulnerabilities relating to the processing, storage, or transmission of cardholder data. This process aims to identify, measure, and prioritize risks that an organization might face and helps define strategies to mitigate these risks. Targeted risk assessments are an ongoing practice, not a one-time exercise. How Do They Differ from Traditional Assessments? In previous versions of PCI DSS, the focus was on an annual organizational risk assessment performed annually or when there was a major change to the business. PCI DSS 4.0, however, encourages organizations to take a more strategic approach to the continuous activities of securing payments. This means considering unique business factors, understanding specific threats relevant to one’s operations, and designing controls that effectively address those threats. It moves from a one-size-fits-all model to a more tailored, adaptive approach. In PCI DSS 3.2.1 the term Risk Assessment was used to describe requirement 12.2. In PCI DSS 4.0 the new terminology is Risk Analysis. While many cybersecurity practitioners use the terms interchangeably, Risk Analysis is being used to identify a more complete and accurate measure. NIST SP 800-30 Guide for Conducting Risk Assessments defines the Analysis Approach this way: The approach used to define the orientation or starting point of the risk assessment, the level of detail in the assessment, and how risks due to similar threat scenarios are treated. The intent of the new Targeted Risk Analysis requirement does not replace the need for an organization wide Risk Assessment, you should still do that even though it’s not a PCI 4.0 requirement. By taking the Risk Analysis approach, PCI DSS 4.0 encourages a more thorough treatment of risk while still providing flexibility and avoiding “one size fits all” requirements. The Elements of a Target Risk Analysis: • Identification of the assets being protected. • Identification of the threat(s) that the requirement is protecting against. • Identification of factors that contribute to the likelihood and/or impact of a threat being realized. • Resulting analysis that determines, and includes justification for, how frequently the requirement must be performed to minimize the likelihood of the threat being realized. • Review of each targeted risk analysis at least once every 12 months to determine whether the results are still valid or if an updated risk analysis is needed. • Performance of updated risk analyses when needed, as determined by the annual review. (Source: PCI DSS) Benefits – Why this is better. In PCI DSS 3.2.1, there was only one place that mentioned performing a Risk Assessment. PCI DSS attempts to be more risk based, encouraging merchants and service providers to do a better job of managing risk while providing flexibility in the approach for each requirement. Some of the Security Activities Covered by Targeted Risk Analysis: • Frequency of Malware Scans • Review of all access by application and systems account privileges • Password/Passphrase management • POI device inspection • Log reviews • Vulnerability management • Payment page tampering detection • Training for Incident Response personnel Conclusion Targeted risk assessments in PCI DSS 4.0 represent a significant shift towards a more adaptive and strategic approach to data security. By encouraging organizations to critically analyze their unique contexts and risks, PCI DSS 4.0 aims to drive real, meaningful security outcomes. In a world where threats are increasingly sophisticated and constantly changing, this focus on targeted risk assessments is not just welcome – it’s essential. Start Now: Targeted Risk Assessments in PCI 4.0 are considered best practice until 31 March 2025, and after that, they will be mandatory. Do not wait! It will take some time for your organization to develop Targeted Risk assessments for PCI, the sooner you start the smoother your PCI assessments will be. By: Peter Thornton – Senior Security Consultant – CISSP | HCISPP | ISSMP | PMP | CISA | QSA Contact us for more information about our cybersecurity solutions.


