How Important are Relationships to the CISO’s Success?

Have you ever heard of a CISO or vCISO entering an organization with guns blazing, slinging policy, implementing a new method of identity and access management within the first 60 days, mandating awareness training, and launching phishing simulations without first thoroughly understanding the business, the business culture, and developing relationships with stakeholders? If you have, I’m sure the outcome wasn’t favorable. Let’s explore why relationships are the cornerstone of a CISO’s success. In today’s fast-paced corporate world, the role of a CISO or vCISO goes far beyond technical expertise. Success hinges on understanding the organization deeply and building trusted relationships. Yet, some leaders rush in with sweeping changes, only to face resistance or failure. Why? Because they overlooked the most critical aspect of their role: relationships. HUMANS We are constantly surrounded by individuals from all walks of life, with different genders, races, religions, belief structures, work ethics, upbringings, education, and knowledge. No matter their title, level of education, or position in life, humans experience love, laughter, anger, disappointment, anxiety, and failures. If you identify with any of this, then you might be human. And this shared humanity is precisely what makes relationships so critical in cybersecurity leadership. Before diving into strategies or processes, understanding the people you work with is key. THE CHAMELEON Why a chameleon? Because they are masters of change and adaptation, depending on their environment. CISOs must be chameleons. Like chameleons, CISOs must blend into their surroundings—not to disappear but to observe, understand, and connect with those around them. This skill is invaluable when building bridges across diverse teams and perspectives. Whether or not, in your personal life, you accept people who are different and have different perspectives, personalities, church affiliations, or political views, in business, you must be willing to accept them for who they are and learn to collaborate based on each other’s strengths and weaknesses effectively. As a CISO or any leader, you must adapt to each person you interact with, like a chameleon. This ongoing interaction with your peers, subordinates, or the C-Suite must remain free from stereotypes or judgment. UNDERSTAND THE BUSINESS A CISO who doesn’t understand the business cannot effectively prioritize risks, align with goals, or communicate with leadership. That’s why doing your homework is non-negotiable. I’m doing my homework beforehand, understanding the organization and how they make money. Are they a retailer, bank, manufacturer, or services company? Are they publicly traded or a private LLC? If public, do they have an 8k or a 10k that I glean additional information from? If they’ve filed an 8k, how much did they disclose? What were the circumstances? If they’re a private company, have they been breached? Can I find out what their revenue projections were last year? Did they meet or exceed expectations? Who are their competitors? Who might want to do them harm? Do they transmit, process, or store sensitive information? What intellectual property may they want to protect? What compliance mandates might they be subject to? These questions aren’t just about gathering information—they’re about framing your security strategy in a way that aligns with the organization’s mission and priorities. TIP: Performing this type of homework before being interviewed will surely increase your chances of being hired in the first place. ASSESS THE DYNAMIC Adapting to people is vital, but understanding the organizational dynamic is just as crucial. When I enter an organization as a vCISO, my goal is to learn the culture of the organization and the individuals with whom I will be spending most of my time. Usually, it’s the CIO or VP of Technology, IT manager, DevOps leader, Cloud Architect, or Security Team. I’ll stop here to break down these different roles by personality traits. CIO: What kind of person is he or she? Is she talkative and willing to share the deep, dark secrets of the organization, or does she keep things close to her chest? As I probe for answers related to the organization and the cybersecurity posture, do I feel overprotective of what the team has accomplished, or do I feel frustrated and want to continuously improve? IT Manager: These conversations may start out discussing asset management, identity and access management, change control, connectivity, exposure to the Internet, and who is responsible for what. Get a feeling of whether they will work with you or against you. Discuss what they’re passionate about regarding the security headache they created (Unnecessary Jab) or not. I’ve worked with some IT managers who are very cybersecurity savvy and implement security controls into everything they do. The point here is to build trust and credibility. Educate them without being condescending. DevOps Leader: Well, we all know that developers are a different breed. Extremely smart and focused, able to take a set of requirements and turn it into a robust, well-thought-out interface. They understand version control, dependencies and libraries, APIs, and often multiple coding languages. But are they social individuals? Most of the time, not so much, and if they haven’t taken a secure coding class, the last thing they want to do is hear you tell them how to implement the OWASP top 10. You must adapt to their way of interaction and build trust over time. If immediate changes need to be made, sit down with him or her and help them understand the implications of not making the change. Again, they are very smart individuals. Cloud Architect: Often, these are engineers who saw an opportunity to learn complex, dynamic, and ever-changing new things. This person understands things like Kubernetes, containers, microservices, EC2 instances, S3 buckets, and blobs. Blobs…blobs, what’s a blob? A blob is the Microsoft Azure version of an S3 bucket in AWS or a GCS Bucket in Google Cloud used to store files, media, backups, etc. Work with this person to understand his or her vision for how the architecture will grow and remain resilient. Ask how you can help improve how things are currently being done or make user management more efficient. Who is
Keep Your Friends Close…Your Enemies Closer

“Keep Your Friends Close…Your Enemies Closer” What does this phrase mean from a cybersecurity perspective? The phrase is often used in warfare and if you’ve read Sun Tzu’s The Art of War, you’ll surely understand it from that perspective. However, if you pay attention to the news, you’ll see that cyberwar has become a real global concern. Nation-states like China, Russia, Iran, and North Korea are constantly trying to gain the upper hand, whether from an economic perspective or a strategic governmental power play. It makes sense when we’re talking about global powerhouses, war, and politics. But what does it mean when we’re talking about organized cybercrime, sophisticated hacking groups, or even the small player trying to make a name for themselves? Know Thy Enemy As governments rely on the art of intelligence gathering to learn what their enemies are up to, so should we rely on the art of cyber intelligence gathering to better understand our adversaries. To prepare and be expected to defend against an attack, we must first understand the attacker—their motivations, methods, and capabilities. What if? Suppose we own a large law firm. What might we want to protect? Ourselves, from the criminals we put behind bars? We might purchase a gun… maybe, but that’s not the point. What about the people who require our services to help close on a home, collect on defaulted rent payments, settle a divorce, or litigate a domestic abuse case? All those individuals are, by law, protected by lawyer-client privilege. What would happen if those client records were stolen, exfiltrated and put up for sale on the dark web? It could potentially put clients in danger of retaliation, identity theft, or worse. The Consequences After a data breach, the consequences are usually far more reaching than most people think. Whether you’re a law firm, retail shop owner, manufacturer, bank, or hospital, the list goes on. Here’s what to expect if a data breach were to be successful, from the perspective of the threat actor: Financial Implications (Primary Loss) Employee non-productive hours paid Time and effort spent triaging the problem Third-party forensics investigations Time spent re-imaging devices Equipment replacement Financial Implications (Secondary Loss) Fines and judgements Damage to reputation or loss of customers Loss of competitive advantage Identity monitoring services paid Cybersecurity infrastructure rebuild While reputation and competitive advantage may not result in immediate financial loss, the long-term effects may be equally damaging. Here are a few examples: – Target incurred over $200 million in settlements, legal fees, and fines. Foot traffic also declined in the days following the 2013 breach. – Equifax spent approximately $1.4 billion in legal fees, settlements, and regulatory fines following its 2017 breach. It also faced lawsuits and loss of customer trust. – Sony incurred around $35 million in remediation costs and suffered from reputational damage among Hollywood professionals. Getting Closer to the Enemy Who, what, when, where, tactics, techniques, and procedures: Who Get to know who the adversaries are. Are they state-sponsored hackers? Are they organized and well-funded due to extortion or ransom payments over the years, like LockBit, REvil, Conti, Lapsus$? What What are their motives behind the attacks? While the ‘Anonymous’ group may be motivated by all the wrongdoings in the world, aiming to disrupt society or governments through hacktivism, North Korea’s state-sponsored ‘Lazarus’ group might be looking to steal military secrets. LockBit, on the other hand, might simply be in it for the money—rumor has it their leader enjoys fancy cars and yachts. When When are they coming for me? Wouldn’t you like to know? There may be an indication from industry competitors or partners. If one of them gets breached, you may be next on the list. Time to cross your t’s and dot your i’s, close the gaps, and patch your systems. Tactics What are they trying to achieve? Are they purchasing access through an access broker to steal your customer database, or are they trying to maintain persistence, moving laterally and gathering up as many usernames and passwords as possible to sell on the dark web? Techniques Does the threat actor or group like to use phishing emails in hopes that you’ll be tricked into clicking the link to re-log into a fake Microsoft account? Or are they watching and waiting for a new vulnerability to emerge in Apache so they can gain access to your web server? Procedures The attacker may use phishing techniques to create fake login pages to harvest user credentials or send spear-phishing emails with malicious attachments, directing victims to websites hosting exploit kits. Conclusion There are tools available that monitor the dark web so you don’t have to. These tools help you develop virtual relationships with the enemy, keeping you better informed and ready when they start peeking around the corner at your building. Tools like Recorded Future help us understand who the active criminals are, what tactics, techniques, and procedures they rely on, or whether they’re targeting your industry—enabling you to be proactive, not just shooting in the dark. By: Brett Price – Lead Cybersecurity Consultant – C|CISO, CISSP, CISM, CISA
Why CISOs Should Pay Attention to Daily Threat Intelligence Feeds

Determining the ROI of your security stack can often be a challenge, so it may come down to staying one step ahead of your competition, minimizing the “blast radius” in the event of a breach which ultimately reduces the financial impact to the organization, or simply providing enough layers of security that the threat actor moves on to another victim preventing financial, reputational, and customer impact all together. Regardless of the motivation to invest in cybersecurity staff, or the latest new Data Security Posture Management (DSPM) solution for identifying, classifying, and segmenting your cloud data, reducing risk to an acceptable level should be a priority in the mind of the CISO. Are We Going to be Targeted Today? We’re all aware that it’s not a matter of if, but when. So much so that it has become cliché. We also can’t predict when we’re next on the list of threat actor targets or coming up on the automated reconnaissance script running nonstop from a remote botnet scrubbing for zero-day vulnerabilities. Routine Risk Reduction As CISOs we may follow a routine of updating policies, reviewing new compliance mandates, planning tabletop exercises, or the annual penetration test. We may prepare for the next board meeting by reviewing overall vulnerability remediation efforts, incident response metrics, KPIs, and KRIs, all to demonstrate our risk reduction strategy, but are we monitoring threat actor activity daily? Targeted Risk Reduction There is an array of threat intelligence tools to choose from such as Recorded Future, ThreatConnect, Mandiant, and the new CrowdStrike Counter Adversary Operations (CAO). There are also free intelligence feeds like the Information Sharing and Analysis Center (ISAC), Cybersecurity & Infrastructure Security Agency (CISA), and FBI InfraGard, to name a few. The data is out there so we should use it to become more targeted in our efforts. Below are recommended approaches for taking advantage of threat feeds and using them to reduce risk where it counts most, exactly where the threat actor is going to attack YOU. Intelligence Analysis Recommendations Know your organization – what industry and where are you exposed? Understand who the most likely attackers are – RansomHub, LockBit, Lazarus Group, Blue Delta, North Korea, Iran, Russia, and China. Understand the most likely methods of attack – Social Engineering, Ransomware, Zero-Day Exploits, Supply Chain Attack or Business Email Compromise. Prioritize vulnerability remediation – Currently being exploited, exploitable, exploit available Who is currently being targeted – Identify whether your industry is a current target. Are your competitors being targeted – Have your competitors suffered a breach in the past year or two? Tactics, Techniques, and Procedures (TTP) – What methods are being used to attack your industry? Are they performing living off the land, utilizing remote exploits, or performing phishing attacks? How? Deep fakes, malicious Microsoft login screens, smishing for MFA codes following a credential theft, etc. Prioritize remediation and mitigation based on your threat intelligence findings. Conclusion Most CISOs are underwater when it comes to workload so sometimes it comes down to simply taking action to reduce the blast radius of an attack and minimizing the impact to the organization. While you work through your tactical and long-term strategies, it’s worth taking time each day to review threat intelligence feeds and act on the findings that may impact your industry or your organization itself. By: Brett Price – Lead Cybersecurity Consultant – C|CISO, CISSP, CISM, CISA
Beyond Red, Yellow, Green: The Evolution of Cybersecurity Risk Measurement

Introduction For years, companies have relied on qualitative methods, if any, to measure cybersecurity risk within their organizations. These methods often involved subjective red, yellow, and green 5×5 matrices or semi-quantitative ranges like 1-5. While these tools provided a basic framework, they often left executive leadership with more questions than answers. This was particularly problematic since CEOs and board members typically had limited understanding of cybersecurity terminology and the controls implemented to protect their assets and sensitive information. Growing Accountability in Cybersecurity In recent years, accountability in cybersecurity has sharply increased. Gartner’s Prediction: In September 2020, Decipher cited Gartner, stating, “By 2024, as many as 75% of CEOs could be held liable for data breaches if it is found that the incidents occurred because the organization did not focus on cybersecurity or invest sufficiently in cybersecurity.” High-Profile Cases: Uber’s Chief Security Officer: Charged for Covering Up Hack: In 2020, Joseph Sullivan, the Chief Security Officer of Uber, was criminally charged due to the actions he took following a data breach. This case underscored the potential personal liability that security officers can face in the wake of cybersecurity incidents. Drizly and the FTC: Ignoring Warning Signs: In October of 2022, the Federal Trade Commission (FTC) took action against Boston-based Drizly, a subsidiary of Uber, and its CEO James Cory Rellas. The action was due to Rellas’ neglect in responding to prior warning signs, which eventually led to a breach exposing 2.5 million consumer records. This incident highlighted the consequences of ignoring cybersecurity risks. SolarWinds: Misleading Investors: In November of 2021, SolarWinds and its CISO, Timothy Brown, were charged with misleading investors following a major cyber incident. This case demonstrated the serious implications of not being transparent with stakeholders about cybersecurity vulnerabilities. The Need for Quantifying Cybersecurity Risk These incidents highlight the critical need for quantifying cybersecurity risk. CEOs and boards are becoming more cybersecurity savvy and expect concrete data to make informed decisions. SEC’s Proposed Rule (March 2022): Requires public companies to disclose whether their boards include members with cybersecurity expertise. Shifting Expectations No longer will executive leadership accept vague PowerPoints with pretty red, yellow, and green boxes or technical CISOs lacking business acumen. They will expect to hear things like, “we can reduce the impact to the organization by $230,000 annually if we implement control X costing $90,000.” Or “Y nation-state group is currently targeting Z vulnerability in our industry potentially leading to an organizational impact of $20 million. We can reduce the risk by 80% by mitigating the vulnerability within our systems for $300,000 annually.” Quantifying Risk: The Way Forward To meet these expectations, organizations need to adopt rigorous methods for understanding and communicating cybersecurity risk. Understand the threat landscape within your organization by defining loss probabilities to include upper and lower bound estimations. Perform likelihood and impact calculations using Monte Carlo simulations. Become educated on a method that has been around since the early 2000s, Factor Analysis of Information Risk developed by Jack Jones. Valuable Resources: Several publications can help understand the global threat landscape and cost of data breaches by industry, such as: the Verizon Data Breach Investigation Report (DBIR) and the IBM-sponsored Ponemon Institute’s ‘Cost of a Data Breach’ report. Monitor threat intelligence feeds and other publications for regulatory fines delivered or overall breach recovery costs. Conclusion To be an effective CISO in 2024 and beyond, a CISO must possess a deep understanding of policies and standards, incident response, recovery point/time objectives (RPO, RTO), security architecture, tools, and technologies. They must also learn the language of the C-Suite, in order to effectively communicate risk in the way of what the businesses care about most, public and personnel safety, financial stability and profitability. This shift from qualitative to quantitative risk measurement is essential for making informed decisions and protecting organizational assets in an increasingly digital world.
Top 5 Threat Actor Groups and Their Modus Operandi

Everyone reading this blog should be familiar with the most notorious and sophisticated cybercrime gang in history, LockBit, targeting over 2,000 victims, receiving over $120 million in ransom payments with other ransom demands totaling hundreds of millions. You may also be aware that on February 20, 2024, the Department of Justice announced that in a joint effort between the U.S., United Kingdom and other international law enforcement agencies disrupted the LockBit ransomware group by seizing numerous public-facing websites. By February 28, 2024, the leader of the LockBit gang, code-named “LockBitSupp” announced that they were back online with a new data leak site equipped with “countdown clocks” for its current victims. Ransomware and double extortion have become the modus operandi for a large group of cyber threat actors over the past 7 or so years, although ransomware has been around much longer. These are not the only tactics, techniques, and procedures (TTPs) used to crush some of the largest and smallest organizations in the world. Let’s look at a set of threat actors and their TTPs that you may not be so familiar with. Volt Typhoon is arguably the most dangerous threat-actor group in the world today. Its profound impact is largely due to its substantial scale and its backing of the Chinese government, elevating it to the status of a Nation State actor. But that’s not the worst of it. It is alleged that Volt Typhoon actors have been infiltrating our critical infrastructure using tactics such as living off the land. Living-off-the-land techniques are the most difficult to detect because they don’t use their own files or install any code or scripts. After gaining access, they simply use trusted system tools, like PowerShell or Windows Management Instrumentation (WMI) to stay persistent and undetected. Blue Delta, sound familiar? What if I said, APT28, still nothing? How about Fancy Bear? I thought you’d recognize that one. Well, they are one in the same. Blue Delta is a Russian state-sponsored group that is attributed to the Russian Main Intelligence Directorate of the General Staff of the Armed Forces (GRU) Unit 26165, according to the Recorded Future, INSKIT Group. Blue Delta is known for conducting credential harvesting, spear phishing, network eavesdropping, and other operations directly against its targets. The group also uses a suite of custom tools and open-source tools to infiltrate its targets and extract sensitive information. Targets have included the Microsoft Email System, the Democratic National Committee, and many others. MarjorNelson, you might be thinking of the charismatic actor Larry Hagman, who portrayed Major Anthony Nelson on ‘I Dream of Jeannie’. However, this individual is a nefarious threat actor associated with the ShinyHunters organization, responsible for posting a 73-million-line database from the recent AT&T breach. The methods most used here are identity theft, phishing, social engineering and SIM card hijacking. FIN7, otherwise known as Carbon Spider, is a Russian Advanced Persistent Threat (APT) group primarily targeting the United States. Its software was said to be used in the Colonial Pipeline attack in May of 2021 perpetrated by the DarkSide group. Since 2015, FIN7 has stolen more than 16 million payment cards—many of which have been sold on the dark web where the purchaser would use them to purchase goods and services. FIN7 is a very sophisticated group using an arsenal of constantly evolving, complex malware tools and TTPs, controlling infected computers through a web of compromised servers around the globe. They operate a ‘legitimate’, in appearance, cybersecurity business called Combi Security in an attempt to hide their nefarious activities. ALPHV/BlackCat claimed responsibility for the December 2023 breach of Vans, a VF Corp company, affecting 35.5 million customers by exfiltrating personally identifiable information (PII) and posting it for sale on the dark web. The group’s modus operandi is ransomware-as-a-service (RaaS), where they sell their software and infrastructure to criminal affiliates who carry out ransomware attacks on victims. The ALPHV group has been responsible for numerous ransomware attacks targeting industries such as manufacturing, healthcare, retail, energy and IT. In Conclusion: There are many dangerous and very active threat actor groups out there, ranging from state-sponsored entities, to sophisticated well-run corporations, as well as script kiddies so this is not considered an exhaustive list. An important takeaway from this blog is that every organization, regardless of its size, is susceptible to breaches and may face catastrophic consequences as a result. CL0P Ransomware Group, Lazarus Group, Storm-0558 are also opportunistic hunters, so remember to: Conduct a Risk Assessment Prioritize and Patch Segment your Network Implement Endpoint Detection & Response Utilize Complex Pass Phrases Implement MFA Minimize Internet Exposure Have an Incident Response Plan Perform Tabletop Exercises Train your Users (Security Awareness) Test your Users (Phishing Simulation) By: Brett Price – Lead Cybersecurity Consultant – C|CISO, CISSP, CISM, CISA Contact us for more information about our cybersecurity solutions.
NIST CSF 2.0 – Why the Addition of GOVERN is Critical to Addressing Today’s Cybersecurity Risk
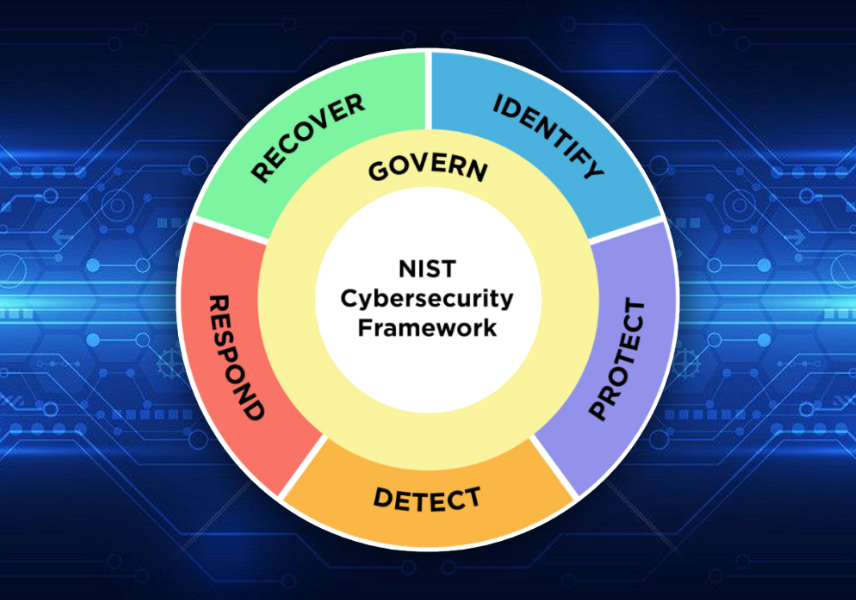
Executives Take Notice In recent years it has become quite evident that a cyberattack can rear its ugly head at any time, affecting organizations of all sizes. It has been said that 60% of small to mid-sized businesses will fail within 6 months if certain risks are ignored. This should most certainly be an executive-level concern considering that a successful cyberattack can result in the loss of valuable data, leading to financial losses, fines, reputational damage, and legal liabilities. Governance Cybersecurity Governance is a process whereby senior leadership oversees strategic control over business processes, and functions through policy and delegation of authority, ensuring an organization’s cybersecurity program aligns with the business mission, goals, and objectives while maintaining compliance with laws and regulatory standards. NIST CSF 2.0 (GOVERN) The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored. Understand and assess specific cybersecurity needs. Every organization has a unique risk profile defined by industry and organizational people, processes, and technology. It is important to understand the specific cybersecurity needs, and to discuss the current and predicted risk across the organization collaboratively determining the level of risk to which the organization is willing to accept (Risk Appetite). Develop a tailored cybersecurity risk strategy. Developing a tailored cybersecurity risk strategy should be based on the organization’s specific cybersecurity objectives, the risk environment, and obtaining feedback from industry peers. The risk strategy should be managed, updated, and discussed at regular intervals. As the environment changes and new processes and technologies are adopted, so does the risk profile. All roles and responsibilities must be clear, maintaining consistency with messaging and delivery. Establish defined risk management policies. Policies have always been hit or miss with many organizations we’ve been a strategic partner with. Some are missing key policies, and some have drastically outdated policies. It is important to establish and maintain risk management policies. Policies should be easy to read and understood by everyone in the organization. Policies should align with the current threat environment, risk profile, and mission objectives. As the risk profile changes, the policies should be updated, and disseminated by leadership throughout the organization. Develop and communicate organizational cybersecurity practices. Communicating cybersecurity practices is vital to adherence through continuous and straightforward communication. This includes policy dissemination acknowledgement and acceptance, and periodic user awareness training. Establish and monitor cybersecurity supply chain risk management. Supply chain risk has gained increased attention over the past few years so it’s important to establish strategy, policy, and roles and responsibilities. Incorporate cybersecurity requirements into contracts that are monitored throughout the life of the relationship. Involve partners and suppliers in planning, response, and recovery. Implement continuous oversight and checkpoints. Implement continuous oversight and maintain checkpoints for continuous monitoring of changes to the risk profile that may need to be included, updated, or redacted. Conclusion Every organization struggles to appropriately address cybersecurity risk while keeping up with regulatory compliance mandates. By understanding organizational context, developing a risk management strategy, defining roles and responsibilities, policy development, oversight, and addressing supply chain risk, you can begin to identify, define, and implement a risk treatment plan. All levels of the organization should be involved in the risk treatment discussion. Determining whether to mitigate, accept, avoid, or transfer risk may be the difference between longevity or failure of the organization. By: Brett Price – Lead Cybersecurity Consultant – C|CISO, CISSP, CISM, CISA Contact us for more information about our cybersecurity solutions.
Cybersecurity Incident Response Programs: Are They Really That Important?

Have you truly considered what it would take to minimize the impact on your organization following a cyberattack? You’ve probably heard the phrase, “it’s not a matter of if, but when.” After hearing that phrase, you may have thought to yourself, “I’m too small for a hacker to care about me,” or “I have impenetrable defenses,” or “I don’t have anything worth stealing.” Let’s dissect them one at a time: “I’m too small for a hacker to care about me.” This is probably the most dangerous belief because it’s the small to medium sized businesses that, if hit with Ransomware, may incur catastrophic expenses during recovery, forcing them out of business. “I have impenetrable defenses.” If you read our blog ‘Cybersecurity Risk is a Business Problem,’ you may have read, “Risk, We can’t avoid it, and we can’t eliminate it.” This holds true for every organization, large and small. Organizations that spend tens of millions of dollars on cybersecurity posture management are still susceptible to cyberattacks. Just ask FireEye, one of the world’s top cybersecurity companies. “I don’t have anything worth stealing.” Often, this is the same company that thinks like the first one. Is your business worth saving? Are student records not worth keeping secret? If unsure, ask the parents or the students themselves. How would your clients feel if they learned their legal history was compromised? Do you accept credit cards, or maintain patient health records? What about your employee’s personnel records or company financial statements? If you answered yes to any of these, then keep reading. What does an incident response plan have to do with it? The quicker you can identify, contain, and eradicate the attacker, the lesser the impact will be on the business. Keys to an effective incident response program: • Understand your architecture – Know your potential entry points – Know where your segmentation boundaries are – Know where your networking devices are – Know where your security devices are – Know where your critical assets and data reside • Train your staff – Security awareness programs – IR Tabletop exercises – Threat Intelligence feeds – Communication and outreach • Write an Incident Response Policy. Have it signed off on, disseminated, and enforced by senior leadership. The policy may include the following: – Statement of management commitment – Purpose of the policy – Scope of the policy (to whom and what it applies and under what circumstances) – Definitions and related terms – High-level Roles, responsibilities, and levels of authority – Incident Identification and Classification – Performance measures – Compliance – Policy Exceptions • Develop an incident response plan to include the following: – Mission – Goals and Objectives – Senior management approval – Roles and responsibilities – Incident categories and classifications – Communication specifics and call tree flow – Incident response plan activation – Location of Procedures and Playbooks – Incident response plan phases • Preparation • Identification • Containment • Eradication • Recovery • Lessons Learned – Document Control – Metrics for measuring the incident response capability and its effectiveness – Approach to Lessons Learned following an incident The Incident Response Policy and Plan should be the foundation for your IR Procedures. The IR Procedures are the step-by-step instructions on what to do if a cybersecurity incident were to arise. Incident Response Playbooks may accompany the Procedures. Playbooks are instructions on what to do in the event of specific attacks, such as malware outbreak, ransomware, or attack on a web server, database, or endpoint. Once these steps have been well planned, aligned with your organization’s mission, goals, and strategic cybersecurity objectives, and have senior leadership acceptance and signature, it’s time to develop the team’s muscle memory. What is muscle memory and what does it have to do with Cybersecurity Incident Response? Muscle memory is what naturally develops when an action or behavior is performed repetitively. Kind of like driving a car. You break when an object gets too close. You put your blinker on before making a turn, well some of us do. You buckle your seat belt when first entering the vehicle. These are all things most people don’t consciously think about. This is precisely what you want to develop once you’ve created your program, which is done through Incident Response Tabletop Exercises. You don’t want your stressed-out incident responders trying to recall what to do next. It should be automatic and without conscious thought. The moral of the story is this: even though you may not have budget approval for all the cybersecurity bells and whistles to Identify, Protect, Detect, Respond, and Recover from a cybersecurity incident, you should strongly consider, and champion for, an Incident Response Program. By: Brett Price – Lead Cybersecurity Consultant – C|CISO, CISSP, CISM, CISA Contact us for more information about Incident Preparedness Services from AccessIT Group.
Cybersecurity Risk is a Business Problem

Risk Consider the fact that we, as humans, assess risk daily. We assess risk before walking across the street, catching a train, driving our car, or even eating spicy foods, so why have we been reluctant to consider cybersecurity risk assessments as the foundational approach to security and assurance? Organizational Risk Let us first discuss business risk. These risks have traditionally been the focus of the CEO, CFO, or COO, and are handled as such. When we think of business risk, we consider things like new competitors entering the market, decreasing market share, rising interest rates, and financial risks such as profit & loss, cash flow, M&A, and credit risk. Market risk may include rising interest rates, foreign exchange, equity, and stock market holdings. Then there’s Liquidity risk and Operational risk. I think you get the point. Cybersecurity Risk When we think of cybersecurity risk, we may think of environmental issues affecting data center operations, like climate control failure, a broken water pipe, data center fire, or smoke.The CISO may be tasked with calculating the probability of risk involving acts of nature such as lightning strikes, floods, tornados, earthquakes, tsunamis, hurricanes, or volcanoes. All are heavily dependent upon the organization’s geographic location. There are regulatory risks, in that, if your organization is breached and found non-compliant, you may be subject to fines and/or refuted insurance claims, or a rise in interest rates. This may lead to reputational damage, loss of customers, or loss of market share. Lastly, we may store intellectual property, such as engineering diagrams, new product releases, software code, etc. so we must consider the risk of it being leaked to a competitor or sold on the dark web. Based on the information covered in the previous few paragraphs, can we not conclude that all are in some way linked to overall business risk? And if we can agree on that, can’t we agree that Cybersecurity Risk is a Business Problem? Cyber Risk Defined There are many definitions of cybersecurity risk out there. If you’ve studied for your CISSP, you may have seen risk = threats x vulnerabilities, or risk = probability of harm * severity of harm, which translates to likelihood + impact. If you’ve studied the CRISC curriculum, you may have read the definition of Risk as the possibility of harm that can come to an asset or an organization. Through my studies, and my knowledge of NIST SP 800-30 ‘Conducting a Risk Assessment’, I have defined Risk as the Probability/Likelihood that a Threat Actor/Threat Source initiates a Threat Event (Tactics, Techniques, and Procedures (TTPs), exploiting a Vulnerability that causes an adverse Impact to the organization. See the figure for a graphical representation. Why a Risk Assessment? We’ve acknowledged that risk is a business problem and discussed business and cybersecurity risks that may be of concern to your organization, but I’m going to list out a few reasons why a risk assessment may be an integral part of your security program: Compliance Mandates Determine Vulnerability Posture Understand Potential Threats Increased Awareness Mitigating Future Risk Cyber Insurance Allocation of Funds Prioritizing Control Selection Risk Assessment Approaches We’ve established a few compelling reasons for performing a risk assessment. Now you may be asking, but what are my options? This question is difficult to answer because it depends on several factors. One is senior leadership’s definition and perspective of risk and risk tolerance and/or appetite. Two is what the expected timeline is for the risk assessment. Three, if performed by a third party, what is the allocated budget for the risk assessment? Lastly, are you assessing an entire organization or a sample set? These questions need to be analyzed and are unique to each organization. That being said, let’s discuss the options. Qualitative – most of you reading this may be familiar with red, yellow, green, or 5×5 risk matrix based on likelihood and impact, in most cases. It may look something like this: Semi-Quantitative – This type of assessment associates a numerical value with High, Medium, Low, or if you’re following NIST SP 800-30, Very Low, Low, Moderate, High, or Very High. These are considered Qualitative Values but if we take Very High, for instance, it may be associated with a value of 96-100 or simply 10. The diagram below illustrates this with more clarity. Quantitative – This method is more complex and time-intensive. It requires calculating probabilities based on upper and lower bound estimates, and confidence coefficients. Some use the Factor Analysis for Information Risk model (FAIR), while others use the Monte Carlo simulation models or Bayes probability theorems. The Process According to NIST 800-30 Step 1: Preparing for the Assessment – Defining organizational risk, risk tolerance, and assessment method. determining purpose and scope. What potential constraints may be associated with the assessment? Step 2: Conducting the Assessment – Identify threat source, characteristics, and events. This step is where you may review ISACS, Threat Intelligence feeds, the DBIR, or the Ponemon Institute’s ‘Cost of a Data Breach’ report to determine industry-specific financial impacts, then apply this intelligence to your organization. I like this aspect of NIST’s Risk Framework because it reduces a bit of subjectivity that exists with a strictly Qualitative or Semi-Quantitative assessment and provides clarity and justification to the board members who may be reviewing the assessment. Identify Vulnerabilities and Predisposing Conditions – gathering software, hardware, physical or logical vulnerabilities, and residual risk left over from a prior engagement. Determine the Likelihood of Occurrence – also an artifact from your intelligence gathering and the assessment and ranking of each assessment category. Determine the Magnitude of Impact – potential regulatory or legal fines, loss of business, insurance premium increases, degradation of production time. Determine Risk – the culmination of the above based on the sum of all data gathered and levels selected. Step 3: Communicating Results – In a prior post, ‘The Modern CISO: From Data Closet to Boardroom’, I mention the delivery of cybersecurity information and assessment results to different audiences. If you’re presenting
The Modern CISO: From Data Closet to Boardroom

In the short span of twenty years, companies of all sizes have experienced rapid transformation in the way they receive, process, store, and transmit data of all types. The most heavily impacted data sets have been personal health information (PHI), financial data, and personally identifiable information (PII). The CISO and security practitioners’ job is, and always has been to protect the confidentiality, integrity, and availability of that data. But what has changed to add such complexity and alter the CISO dynamic so drastically compared to twenty years ago? Sparse Beginnings In the early 2000s, CISOs were few and far between. Many security professionals with the acumen and interest to learn something new evolved from IT-related roles, such as IT managers, system admins, or network engineers. These individuals were tasked with protecting, what I often refer to as, the hard candy shell of the organization consisting of nothing more than a firewall, anti-virus, and in some cases, signature-based Intrusion Detection and/or Prevention Systems (IDS/IPS). The biggest perceived focus for many of these individuals was protecting their organization from the evolving prevalence of nuisances, such as script kiddies. The firewall protected the outer shell from the bad guys on the Internet, and the AV solution identified and eradicated viruses that got through to the soft center, usually through opened email attachments, and the IDS/IPS gave some visibility into failures of the other controls. The technology worked fairly well if the vendor updated the hard-coded signatures in a timely manner. Whack-A-Mole As security vendors developed signature-based virus detection tools and intrusion detection and prevention systems to thwart the script kiddy, veteran threat actors also began to adapt by making small modifications to their virus and malware code to evade detection. The industry soon followed suit and developed anomaly-based detections. This back and forth still goes on to this day, only much more sophisticated methods are used today. Regulatory Compliance and Security Standards The introduction of Federal Government regulations and non-government enforced Standards began changing the way organizations looked at data from a handling and storage perspective. The CISO soon became a check-the-box senior practitioner or director and was responsible, along with the IT and Legal teams, for sorting through government regulations and industry standards and determining a path forward. In addition to some of the earlier laws enacted, such as the Computer Security Act of 1987 focusing on the security of U.S. Federal Government systems and the Privacy Act of 1974 requiring certain data types be identified and secured, we began experiencing the transition from walls of filing cabinets to digitization and storage of records that accompanied new laws and regulations such as the Health Insurance Portability and Accountability Act of 1996 (HIPAA), finalized and published in December of 2000, the Gramm-Leach-Bliley Act, enacted in 1999 for the financial industry, and the Sarbanes-Oxley Act of 2002 for publicly traded companies. In 2004, five of the major credit card companies, Visa, Master Card, American Express, Discover, and JCB, joined forces and created the Payment Card Industry Data Security Standard (PCI-DSS) due to the costly rise in credit card fraud. Add in the EU General Data Protection Regulation (GDPR) mandating the protection of data identifying individuals (PII) of the European Union and you have a diverse mix of regulatory soup that requires a dedicated individual or team of individuals to stay on top of. This either forced the propeller head out of the leadership role or required a great deal of learning on the fly with mixed results. Please don’t take offense. I was one of those propeller heads back in the day. I have evolved! All the Buzz Without getting into the entire history and evolution over the past two decades, discussing the digital transformation age, rapid public cloud adoption, zero trust, and artificial intelligence— which are often loosely defined and over-utilized buzzwords by security vendors and are too many to list as of 2023—Cyber Espionage, Ransomware outbreaks, data leaks, credential theft, and exposed databases, let’s understand how and why the CISO’s job has continued to evolve and become more complex. The Holistic Approach You may have heard the phrase or a variation thereof, “Being compliant does not make you secure, and being secure does not make you compliant”. This is where a holistic approach to cybersecurity must be strategically considered. While you’re performing tool rationalizations and performing risk assessments based on NIST 800-30, you may also want to consider either a maturity-based framework such as the Center for Internet Security’s Critical Security Controls Version 8 (CISv8) or a risk-based approach such as the prescriptive NIST 800-53 or the heavily adopted NIST CSF. Any of these frameworks provide a holistic and strategic approach to security, allowing you to assess your current posture and set short-, mid-, and long-term goals, improving your posture over time. The bonus to adopting and working through these non-regulatory frameworks is that you will be addressing many, if not all, of the regulatory requirements as you go. They also force you to avoid the “boil the ocean” approach, which often leads to disaster. The Top-Down Approach Prior to the late 2000s, most organizations took a bottom-up approach to security by reacting to incidents that occurred either within their own organizations or industry partners. Organizations would react by implementing technology and solutions that would give them a warm fuzzy feeling during the next virus outbreak, credential mishap, or malware ingested from a USB stick found in the parking garage. Very few organizations considered governing their security programs from the top down by developing policies, standards, and procedures and then enforcing them with full cooperation of and dissemination by C-Suite leaders of the organization. Presenting to the Executive Suite and Boardroom Have you ever gone into a board meeting with a polished presentation and started talking about technology or how the latest and greatest Ransomware prevention tool will reduce risk and move the 5×5 color matrix from a bright red box to a light red box if they give you funding?
October: National Cybersecurity Awareness Month

Cybersecurity Awareness Month is a collaboration between government and private industry to raise awareness about cybersecurity and empower everyone to protect their data from digital forms of crime. In the spirit of Cybersecurity Awareness Month, we thought we’d share 10 simple tips we all can use to protect ourselves from security risks while at work. By following these tips for personal cybersecurity, we hope to help you increase your ability to protect yourself against sophisticated hackers and stay safe online. 10 Personal Cybersecurity Tips & Best Practices Tip #1: Understand Your Companies Policies and Procedures As a remote worker or someone who travels for their job, it is essential that you follow your company’s policies and procedures for working remotely. Ask your manager for your organization’s Work From Home (WFH) or Remote Work Policies. It is your responsibility to acquaint yourself with your employer’s policies and procedures for working remotely. Tip #2: Protect Your Passwords Password safes are very abundant and many good password vaults are free. Download one on your phone and your workstation. Some password vaults can sync between your phone and workstation. Think of a passphrase that is 14 characters long and includes letters, numbers, and characters. If you can use multi-factor authentication, use it for sensitive web-based portals, bank accounts, or anything that may cause harm to you if exposed. Once you get used to your password vault, it will become second nature and may save you a long battle reclaiming your identity. Tip #3: Keep your Devices and Software up to Date Adversaries are very aware of new vulnerabilities and pounce when an exploitable vulnerability is identified and released to the public. Advanced adversaries continuously attempt to identify zero-day vulnerabilities, meaning they have identified a weakness in firmware or software before the vendor has released a patch. Most vendors prompt you or auto-update software. Either way, make sure you’re up to date. Tip #4: Use a Secure Wireless Network Avoid using public WiFi whenever possible. Hotels, airports, and coffee shops are a common playground for the bad guys. Your phone may have personal hotspot capabilities so it’s advisable to set it up using a strong password. When setting up your home WiFi, be sure to configure strong encryption like WPA2 or WPA3. Turn off the SSID broadcast to make it a little more difficult to detect, and use strong passwords. Tip #5: Utilize Video Conferencing Security Practices Video conferencing tools are a remote worker’s lifeline. Secure your meetings by establishing a password, creating a waiting room, and locking down your meetings once they’ve started. Also, be sure to check your surroundings for any disclosure of sensitive information that may be within your camera’s view. Tip #6: Practice Responsible Social Media Use While social media has its benefits, it can also pose risks as employees’ online behavior can have serious consequences. • Take the time to review your employer’s Social Media Security Policy. • Be wary of fake ads and suspicious links. • Refrain from posting private details about your employer or your location. Adversaries glean information from social media, Google searches, address lookups, next of kin, friends, bosses, you name it. They do this to be as convincing as possible when phishing for your password to break into your accounts, perform SIM swapping for SMS MFA tokens, spoofing emails to send to your friends making it look like you’re asking for a favor, sending you a web link laced with malware. The list goes on, so be careful what you post and who you connect with. Tip #7: Build a Secure Workspace Take security precautions to protect your organization’s information, network, and devices just as you would in the office. Be sure to lock your computer when you step away and use a locked file cabinet to secure confidential documents. Antivirus/Malware software is abundant and most come with a workstation antivirus, malware, and ransomware protection, desktop firewall, account protection, and browser safety controls. If the cost seems excessive, consider how much you could potentially lose without it. Tip #8: Be Aware of Social Engineering Scams and Tactics Hackers will exploit your trust to trick you into giving up valuable information via email scams (or phishing), phone scams (or vishing), and malware-infected flash drives. • Don’t click on unknown links and downloads. • Never share personal information such as your birthday, social security number, and bank information. • If you think you’ve been socially engineered, report it right away. Tip #9: Be Vigilant When Working in Public Places Never leave valuables such as computers, mobile phones, thumb drives, and other storage devices unattended. Never pick a USB drive up off the ground and insert it into your computer. This is a common tactic among data thieves. Once you plug it in, malware quickly jumps from the drive to your computer. From there it’s game on. The bad guys have the keys to your kingdom. If using a personal USB device, put some anti-malware and encryption software on it and password protect it. That way, if you lose it, the bad guys won’t be able to look at your sensitive data. Tip #10: Backup your Important Data USB backup drives are relatively cheap nowadays so you may consider purchasing one as a backup device. Back up your data once a week, unplug it, and stick it in a safe or your desk drawer. If you’re at work, your data is likely being backed up to a cloud storage service. If it will cause you distress if it suddenly vanishes, then keep a backup. We hope that by reading these tips, you’ve become more cyber aware. At the end of the day, it’s our responsibility to proactively protect our online security. Conclusion: If recent breaches tell us anything, it’s that an organization is only as strong as its weakest link. That is why security awareness is critical in protecting both you and your business. Encouraging your workforce to be vigilant about cybersecurity makes a huge contribution towards


